Are you among those seeking insight on creating a transformational digital strategy? Don’t overlook the assumptions on which you are hanging your transformation’s success.
Your transformation proposal is presenting a vision of the future, a future that is an improvement over what exists today. And while your transformation roadmap will be a carefully and thoughtfully constructed plan, its success is not guaranteed. The success of your execution is completely dependent on your assumptions proving to be true. If you present your strategy without expressing your assumptions, you are – intentionally or not – committing to deliver your strategy without respect to hindering or disruptive factors.
Assumptions lie below the surface, pregnant with unspoken expectations. If, in the future, those assumptions prove false this documentation might provide you with an opportunity to renegotiate completion dates or project costs.
What do I mean by assumptions? Consider these:
- Are you assuming that the high-performing leadership team and project managers you command today will remain intact for the multi-year journey that you’re laying out in your roadmap?
- Are you assuming that the fullness of the solution you are proposing will be implemented as-is, without any custom modifications?
- Are you assuming your users will eagerly and enthusiastically adopt your new solution without offering resistance?
- Are you assuming that there will be no external disruptions to your timeline, including geopolitical actions, catastrophic health events, new government regulations, extreme acts of nature (storms, earthquakes, large-scale power outages, etc.)?
These are just a few of the things that could disrupt your ability to deliver the initiative on time and on budget.
Your list of assumptions will create a lively discussion when you present your strategic plan to your fellow executives. You can expect at least one reviewer to state, “We can’t assume that. We don’t know that to be true.” That’s the very reason that you present these assumptions. When such a comment is raised you will have a great opportunity to discuss the considerations necessary to adjust the corresponding expectations (and timelines and budgets) should those assumptions prove false.
Risk
When assumptions prove false, risks are introduced. You are proposing an initiative that will transform your organization. In my book, IT Strategy, I wrote that risks can commonly be divided into five categories: schedule, budget, technology, culture and market dynamics.
Drilling down one more layer in risk identification reveals the need to assign risks to the nine components of, what I call in the book, the Deliberation dimension. This detailed matrix might look like the example below.
Figure 1. Risk Identification Matrix
One effective way to present risks is to use a two-column table, as shown below. The first column would state the risk, and the second column would elaborate the implications of that risk. Management will appreciate that you have taken the time to present both the risks and the implications of those risks. Expect that your reviewers will introduce alternative mitigation approaches, but don’t let that diminish your enthusiasm. These alternatives simply mean that the reviewers are engaged with you in the process.
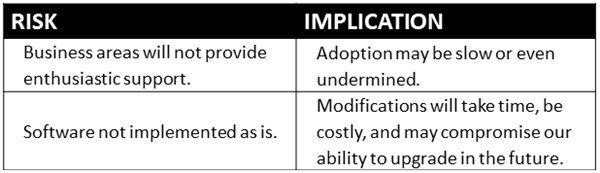
Figure 2. Risk Evaluation Table
Consult Risk Experts
Every business also has established a threshold for risk beyond that it will not engage. You should speak with a knowledgeable expert from the risk management organization in your enterprise to discuss these two topics, specifically as they relate to technology initiatives. Does your company have a risk assessment checklist that each initiative must complete? If so, mapping your strategy’s potential performance against that checklist should be included in the plan. If risk profiles are not currently established for IT initiatives, consult with your risk management expert, and ask them for suggested topics that should be thoughtfully considered as part of your IT strategy.
Risk assessments come into play when you create specifics of your IT strategy and transformation roadmap. Whether your roadmap includes infrastructure upgrades, migration to a cloud provider, or enterprise software upgrades, your strategy probably includes a switchover between old and new environments. Switchovers can introduce disruption to numerous areas of your business. And don’t overlook the risk to schedule and budget that a steep learning curve might present as you train employees in transformed future state processes.
Experienced executives are familiar with risk assessments as part of routine proposal review. They will look for areas where you might have overlooked common areas for disclosure. Failure to disclose risks or choosing to be overly optimistic regarding the risks typically weakens your proposal. As the creator of the strategy, you should convey confidence that your proposed strategy will deliver benefits to the business. Find the balance that presents a realistic assessment of the risks and then present a realistic mitigation plan so reviewers know you have applied due diligence.
How will you deal with disruptions? Some disruptions are self-inflicted or self-imposed. Some disruptions are externally initiated, such as acts of nature. Other disruptions are beyond your ability to control, such as political, social or macroeconomic instability. There should be an acknowledgement that these disruptions are possible and appropriate adjustments will be evaluated and employed in response.
|
Related article: Launching a Transformation and Capturing Its Value By Mahesh Harvu |
Recommendations
The most thorough method to ensure you have considered all reasonable assumptions and risks associated with moving to the future state is to review each of the nine components of in the Risk Identification Matrix (Figure 1 above). Documenting the assumptions and risks regarding data, technology, security, and so on through all nine components will demonstrate your due diligence.
Finally, be aware of the presence of blind spots and confirmation bias. Blind spots are topics in which you either place blind faith or have a limited expertise but choose to conceal your lack of awareness out of pride or insecurity. Confirmation bias is created because people naturally agree with comments that support their preconceived biases and reject comments that don’t align. Review your assumptions and risks one more time to ferret out statements that reflect confirmation bias and blind spots. The goal is to be objective and thorough.
Before presenting your full strategy to your approvers, you’ll find value in having a trusted colleague review your document for reasonableness and thoroughness. This review is particularly important regarding assumptions and risks. Veiled assumptions are those things that you state as fact, but are actually just hopes or hunches that you’ve bundled as givens. It is best to uncover them and address them before you present to executives. Other executives will respond favorably when they see your thorough due diligence complete with your thoughtful recommendations for mitigation. They may have valuable insights to add to yours, and seeking their input pays dividends. Once they make their contributions, it demonstrates their engagement with your proposal and propels your initiative towards approval.

Written by Jim Maholic
Jim Maholic has over 25 years of experience as an IT strategist. His career has included two stints as a CIO, executive positions with Big Four and regional consulting firms, and leadership roles with enterprise software companies. He is an award-winning, bestselling author, having written IT Strategy and Business Cases that Mean Business.



