This article was excerpted from a report the author published recently in Security Current. A full-length version of the report is available here.
The role of the Chief Information Security Officer is highly dynamic and presents great challenges for those that serve in the position. There was a time when the information security leader was a purely technical role, focused on firewall configurations and password policies. While these aspects of information security remain important, the role has matured to encompass business leadership responsibilities.
Today, the CISO is recognized as a crucial member of the executive team, no longer confined to the technical side of information security.
In this new context for the role, these are the ten skills that every CISO must have to be successful, in any and all organizations and industries, today and in the foreseeable future.
1. Communication and Presentation Skills
At any particular time, CISOs must be aware of who their audience is and capable of adjusting how they communicate accordingly.
When working with executive leadership, for example, CISOs must know how to discuss information security in business terms so that it makes sense, and resonates with the executive. Or when working with a non-technical front-line employee, the CISO must be able to explain security concepts in a way that is relevant to the individual’s specific role and responsibilities.
2. Policy Development and Administration
Security policies that are developed, and then set on a shelf, are useful to no one. High performing CISOs are able to ensure that security policies:
- Meet mission strategic and tactical goals,
- Are promulgated throughout the organization,
- Are implementable by the organization and works to positively secure the environment,
- Meet legal and regulatory requirements.
3. Political Skills
The ability to interact effectively within the organization is critical to the success of the enterprise information security program, therefore making political skills important.
The CISO should understand the needs and concerns of the executive team as they relate to the mission of the organization and then present the information security program as a response to these needs.
For peer team members and users, the CISO should communicate that information security findings are not accusatory or punitive, and the policy is not meant to hinder them from doing their jobs. Rather, the security policy exists to help everyone perform their jobs better and more securely.
The CISO should implement a rigorous organizational change management processes to ensure highly effective communication that presents how information security changes are designed to protect the organization and ultimately the jobs of all employees.
4. Knowledge and Understanding of the Business and its Mission
It is incumbent upon the CISO to work with mission leaders ensuring that new security projects have the necessary mission value, and will ultimately contribute to improved organizational resiliency and productivity.
Once this relationship has been established and appropriately communicated to the organization, the CISO should seek out mission leaders to champion and drive new security projects and support the ongoing security activities. In doing so, the security project becomes a mission activity rather than a security.
5. Collaboration and Conflict Management Skills
The CISO is now called upon to collaborate with members of the organization’s mission team, technologists and end-users.
When collaborating with the mission team, the CISO now works with them to solve issues that effect the successful operation of the organization. When working with technologists, the CISO must ensure that security requirements are well explained, and that effective guidance is provided. When working with end users it is important to develop training that drives the adoption of information security practices by the end user community.
|
The Ultimate CISO Job Description by Heller Search |
6. Planning and Strategic Management Skills
How should CISOs engage their organizations to achieve strong support for the information security program?
- First, the CISO should work with the organization’s executive leadership team to ensure that information security planning activities support the organization’s strategic plan and desired risk posture.
- Second, the CISO should understand all the technology projects that are underway and planned throughout the organization. This way, the information security program can work to fully integrate into each project’s system development life cycle.
- Finally, the CISO needs to observe and plan for the changes in the information security technology industry, and manage an information security program that is ever-evolving.
7. Supervisory Skills
A team of effective information security professionals is needed for any robust information security program. It is not just one person – the CISO – but an able group or team that works well together.
Mentoring, and mentoring well, is critical in the cybersecurity field. Working with the team to develop their skills leads to a much more engaged team, and a more effective information security program.
8. Incident Management
Establishing an incident response program that can detect intrusions on the network and immediately work to clean and recover from those intrusions is critical.
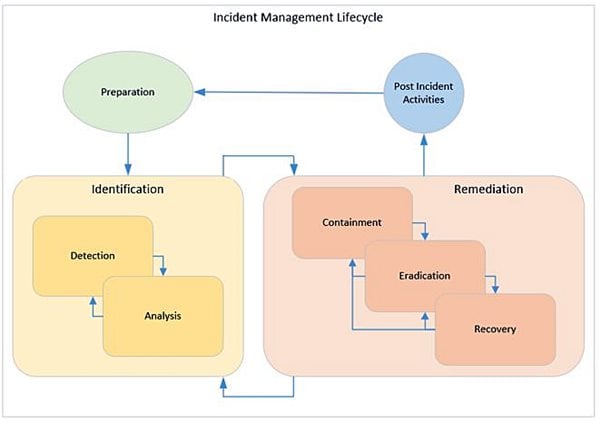
The stages of an effective incident management plan include:
- Preparation: Establishing and executing a well thought out and effective incident response program.
- Identification: The activity of intrusion discovery.
- Detection: Detecting the presence of a malicious actor.
- Analysis: Validating the presence of a malicious actor.
- Remediation: The activity related to intrusion eradication.
- Containment: Ensuring any new information systems cannot be infected.
- Recovery: Eradicating the infection from the information system.
- Mitigation: Ensuring that the information system is configured so that it can no longer be exploited.
- Post-Incident Activity: Lessons learned and continuous improvement.
These stages when implemented correctly establish an incident management life cycle that ensures effective planning, management, and continuous improvement as outlined in the figure below.
9. Knowledge of Regulation and Compliance with Standards
The CISO must be an authority in the regulation, standards and compliance requirements that are most applicable to the organization. This way, the CISO can tailor his research and learning efforts to meet the specific needs of the organization, leading to the development of more effective and relevant information security policies, processes, and procedures.
10. Risk Assessment and Management
Risk assessment and management establish key processes used for communication between the organization’s executive leadership and the CISO.
Risk ownership is always a C-Suite/Board Level/Executive Leadership issue, so establishing a business-level line of communication between executive leadership and the information security program is vital to establishing a risk management program. The risk management program and its outputs must always be aligned with the business to be effective.


Written by Darren Death
A proven technology leader with over 20 years of experience, Darren Death has led, designed, and implemented large-scale, enterprise IT systems at the US Attorney’s Marshalls Service and Alcohol Tobacco and Fire Arms divisions, and the Library of Congress. Currently, Death is Vice President of Information Security, CISO at ASRC Federal, a company that delivers engineering, information technology, and other services and solutions to U.S. civil, intelligence and defense agencies.




