2020 will be remembered as a massively disruptive year. Not only for COVID’s devastating death toll and health implications, but also for how it drove a massive overnight shift in employee work patterns and technology operations. Business applications and related technology moved to the cloud at an accelerated pace and record numbers of employees work from home now full-time. Most of these changes are probably here to stay.
Of course, cybercriminals have gotten into the act too. The result is the emergence of a second pandemic – a cybersecurity pandemic featuring an explosion of global cyberattacks.
As a business technology and cybersecurity advisor in this chaotic time, I am seeing common themes and patterns emerging that will influence how we approach cyber-risk management in 2021 and beyond. After working and collaborating with talented leaders at innovative companies these past 12 months, many of who are blazing new trails in the enterprise risk management/cybersecurity space, here are my top 10 observations:
Cybersecurity Top Ten
- Evolving Cyber Frameworks – The Department of Defense’s new Cybersecurity Maturity Model Certification (CMMC) is being adopted by other government agencies and private sector companies. The new standard features five maturity levels requiring an independent third-party for CMMC certification.
- Machine Learning/Artificial Intelligence (ML/AI) – Automation has supplanted the error-prone human factor, protecting email systems, providing end-point security, and producing security scorecards.
- Contactless - Contactless transaction requirements exposed new potential points of failure and vulnerability.
- Hybrid Work - Hybrid in-office and remote work models necessitated changes to behavior-based analytics to better recognize anomalous behavior. (e.g., it’s much harder to recognize authentic, authorized access vs. compromised access).
- IoT – The proliferation of IoT devices and increased threats exploded. OEMs must now up their game and bake in cyber risk programs in both the hardware and the embedded software components of their products.
- Privacy Concerns Skyrocketed – I am seeing a new specialist role emerge – Chief Privacy Offer. CCPA and GDPR will not be the last regulatory requirements to appear. In the U.S., several states like New York, Washington, and Texas have followed California’s footsteps and adopted new, state-specific privacy laws.
- Cloud - Accelerating cloud adoption rates for business solutions forced companies to take on and own securing their new, cloud-intensive environments.
- Zero-Trust - Zero-trust networks emerged as the new standard for managing employee access to specific applications (replacing traditional VPNs). Castle-and-moat security methods were ousted by zero-trust solutions with their superior focus on holistically gathering information including user identity, device type, and location connection to protect company assets.
- Outsourced Security – Cybersecurity talent shortages drove an increase in managed cybersecurity providers. Organizations moved to providers for security operations, vulnerability management, and employee awareness.
- Employee Awareness – Increased cybercriminal activity and the wave of work-from-home employees thrust cybersecurity awareness into a brighter spotlight than ever. Employers have focused on teaching employees to share cyber awareness resources with family and friends.
Cybersecurity Basics in the C-Suite
Traditional Enterprise Risk Management (ERM) programs have shifted too; it is essential that they become more dynamic and agile to match the pace of business, and the realities of the new cybercriminal landscape. Chief Risk Officers will either have to slow adoption of new technologies to play it safe, or else brave embracing risk effectively if they hope to gain competitive advantage. Whichever choices organizations make, the increasingly complex intersection of ERM programs, cybersecurity enablement programs, and business unit operations requires a holistic approach.
At one company, I helped develop a simple model to showcase the heightened need for collaboration across the enterprise. We emphasized the idea that cybersecurity is not solely "an IT thing”, but a part of the new operating model of the company.
This underscored my long-held belief that digital transformation has moved beyond the walls of IT and into the C-suite. CEOs, CFOs and COOs must expand their understanding of cybersecurity and technology, making it a natural part of their business acumen and strategic thinking. It is no longer an option to plead ignorance about technology and cybersecurity. The implications to company and client success depend on it in today’s new world.
Collaborative Risk Management
The model below highlights the collaboration needed between three key areas within the enterprise. It was originally created by Anne Hungate, founder of Daring Systems. I have a CISO-in-residence role at a company where Anne currently leads technology and transformation. Together we adapted her model to reimagine the new kind of collaboration demanded in today’s risk-based environment. (Thanks to former White House CIO Theresa Payton, who first introduced me to Anne and her model). Here it the adapted model:
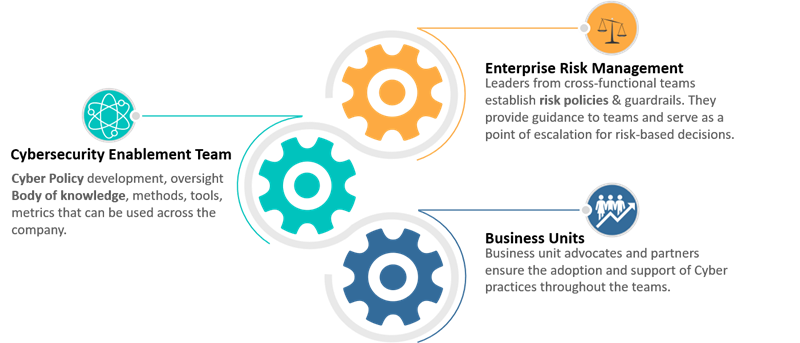
Here is how it works: Starting at the top, with the Enterprise Risk Management (ERM) function, the Chief Risk Officer leads a cross-functional team which develops policies and guidelines governing risk-based decisions for the enterprise. The ERM function then works collaboratively with the Cybersecurity Enablement Team (typically the CISO in larger companies, or the IT organization in small to mid-sized companies) where together they detail cyber policies, methods, and metrics. These policies ensure cybersecurity methods and procedures are consistently applied across the enterprise. The Business Units are the third cog in the model. They put things to work by leveraging the guardrails established by the ERM.
This model’s emphasis on the collaboration between all three areas is what makes it so powerful. In fact, in this COVID-accelerated world of cyber disruption, next-level collaborations like these are the only path to enterprise risk management prowess.
What a year it has been! Change, change, and more change. With more people working from home, more cloud solutions, and the sheer pace of change, it is critical that risk management take on a more collaborative role inside companies. Cybersecurity can no longer be thought of as an IT only program. Organizations that navigate these rough waters will be the ones that view ERM and cybersecurity as a cross-team collaborative effort.
There is always more room to improve on this front – cybercriminals will not wait for companies to wise up. Stay updated of the trends in cybersecurity, map out your game plan and do not hesitate to seek help as you elevate your ERM and cyber programs.


Written by Joe Topinka
Joe Topinka is an award-winning CIO, executive coach, and author with more than four decades of technology leadership experience. He founded CIO Mentor to advise IT and business leaders across industries. Topinka has served as a strategic advisor to Fortune 500 firms, startups, and public agencies. He is a former Board chair and current board member emeritus of the BRM Institute, and the author, most recently, of Beyond the Algorithm: Lead What Machines Can’t, a playbook for accountable, business-minded leadership in the AI era.




