For years, CIOs have resisted, pushed back, and have been frustrated by business units’ propensity to identify and procure business solutions without involving IT. This is commonly known as “shadow IT”.
Historically, shadow IT has pitted IT organizations and business units against one another. But times are changing thanks to the soaring volume of robust cloud solutions in the market, and the arrival of digital natives in the workforce. I advise CIOs to resist the temptation to fight this inevitability and, instead, to embrace it. The truth is that software and service providers are making it easier for digital natives to tap solution capabilities on their own, without IT's direct involvement.
As IT leaders, we must learn a new way to proactively manage this changed reality. And while CIOs grapple with it, business leaders must become savvier in their new role as the solution owner. In many ways, digital transformation is about how business leaders can evolve their understanding of the role technology plays in the success of their company. When non-IT people adopt a cloud solution on their own, their role expands to solution and vendor manager. On that, they could learn a thing or two from their IT colleagues.
Share Your Knowledge and Expertise
IT leaders have been in the vendor management business from the beginning. We know all too well that procuring cloud services is more than just a credit card payment to a vendor, and we have a responsibility to share our decades of experience managing vendor relationships with our business peers. You can do so by proactively helping business leaders understand what it means to take on the role. Provide them with insight into how you manage compliance, privacy, risk, cybersecurity requirements, and ongoing vendor management. Help them see that they too must make these same areas part of their vendor management gameplan.
It is easy for organizations to ignore these requirements until an incident occurs, and your customers and your brand takes a hit. Often in these cases, executives look to IT to step in and help. They may also wonder why IT wasn’t there from the beginning. Therefore, it is helpful to adopt clarifying language that paints a vivid picture of what it means to take on and own a platform.
IT Advocated Systems
When IT is asked by an organization to take on and manage a platform, I call it an Advocated System. This means that the company has sanctioned and approved the necessary resources to proactively manage the platform. The scope of management includes managing risk, cybersecurity, privacy, solution capabilities, integration to other systems, reporting/information services and of course, the vendor relationship. For many business leaders, this is an oft-neglected aspect of their newfound freedom in the digital era.
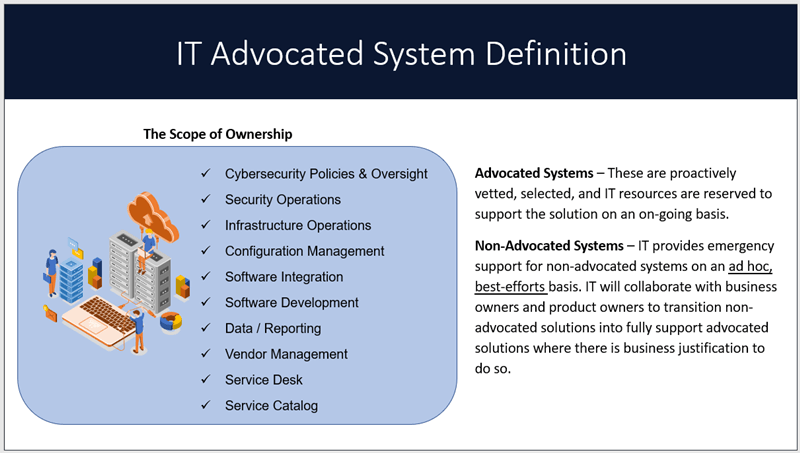
As a CIO, shadow IT solutions would frequently find their way to ITs doorstep. Often the impetus for this stemmed from a business leader that ran into a roadblock where they realized they needed ITs help. Their natural inclination is to come to IT for assistance. They ask for help because they need it – yes – but also because they think that IT has unlimited resources, and that it is IT’s job to help when asked. This is a gap that must be closed as part of digital transformation journey.
Using the advocated systems language, I am sure to let business leaders know that IT is happy to help, but I remind the business leader that IT already has a suite of advocated systems to manage and taking on a new platform requires a business conversation. The fundamental questions that need answering are:
- What resources are needed to take on the platform?
- Are other commitments impacted when doing so?
- What is the business value to the organization if IT takes on the new platform?
Similarly, if a business unit determines they want to own a platform, they need to ask themselves the following questions:
- Does your team have the capacity, knowledge, and expertise to take on management of the platform?
- Are your prepared to own the ongoing care and feeding required to keep the platform or solution vibrant and secure (even when outsourced)?
- Do you understand the risk and cybersecurity requirements to keep the platform safe and secure?
- Does it make sense to for your business area to dedicate time and expense to manage the solution?
Related article:
It’s Time to Stop Whining About Shadow IT
By Mark Settle
The Evolving Role of IT
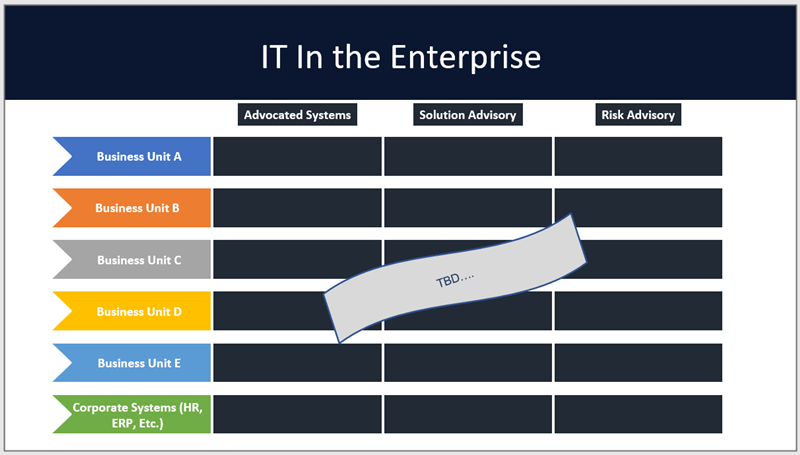
The shadow IT wave is pushing organizations to re-think the role of IT in the enterprise. IT organizations have been on a journey from design-build-run to collaborate-integrate-orchestrate, which I wrote about in The Heller Report in 2019. IT is no longer the sole owner of business applications. To paint a clearer picture of the relationship IT has within the organization and the systems it uses, take time to map out the roles IT plays inside your company. Start with three columns, one for advocated systems, another for solutions advisor, and the last for risk advisor. Add rows for each business unit and corporate functions and then explore where IT plays a role across the three columns in the matrix.
In the cases of non-advocated systems, IT can still contribute significantly to the organization. Specifically, IT can perform a solution advisory role to help business choose the right platforms. IT can also provide vital risk advisory/cybersecurity insight for non-advocated systems: something your enterprise risk team and board will appreciate. Getting this nailed down helps to solidify where IT plays its role and how IT engages with business units. And from an enterprise risk standpoint, it clarifies who the solution owners are and, ultimately, who is accountable for managing vendor risk.
Solution Journey
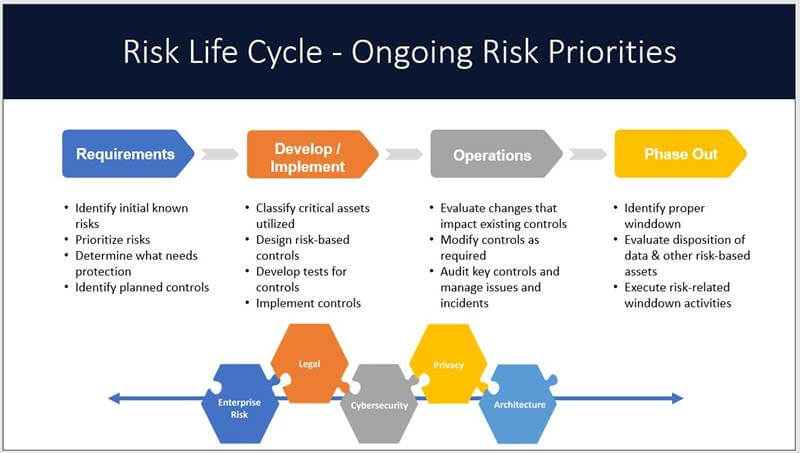
For organizations that are already on this de-centralized IT path, they have realized that it takes effort to “trust but verify” that business units (and IT) are following risk policies and guardrails. As organizations make their way in the digital era, creating a system to vet new solutions requires that solution owners understand the full scope of their expanded role. Enterprise risk, legal requirements, cybersecurity, and privacy are part of the interconnected guardrails that organizations must be aware of when it comes to any solution, cloud-based or otherwise.
When you make the solution decision, the journey is just beginning. Ensure that the right requirements are captured up front and are in place at the beginning of your journey. Once the platform is operational, keeping the solution secure is the responsibility of the solution owner throughout the entire solution lifecycle.
Shadow IT is here to stay, and CIOs and IT leaders must embrace this as a new way of life. The key is to understand the role of a solution owner and be clear about what solutions are advocated and which are not. It is also important to provide a pathway to advocated IT systems so that digital natives know how to transition or ask for help when they need it. This includes making business owners aware of their full set of responsibilities as a solution owner, which stretch well beyond selection and credit card payments for the solution.
The real digital transformation journey that needs to take place is for business owners within organization to evolve their knowledge and understanding of how technology plays a key role in enabling their business strategy. That includes understanding the enterprise risk, cybersecurity, and vendor management requirements that they must undertake when owning a solution.
IT organizations play a key role in providing guidance, knowledge and expertise as a solution advisor and risk advisor for non-advocated solutions. Evolving your organization’s understanding of the enhanced role of a business owner is critical to your success. Your employees and your customers are counting on your organization to embrace this new reality, and to protect them and the company’s assets.


Written by Joe Topinka
Joe Topinka is an award-winning CIO, executive coach, and author with more than four decades of technology leadership experience. He founded CIO Mentor to advise IT and business leaders across industries. Topinka has served as a strategic advisor to Fortune 500 firms, startups, and public agencies. He is a former Board chair and current board member emeritus of the BRM Institute, and the author, most recently, of Beyond the Algorithm: Lead What Machines Can’t, a playbook for accountable, business-minded leadership in the AI era.



